If you’ve been around the Vault community for a while, you’ve probably heard some version of this statement:
“The whole point of Vault is to stop putting sensitive information in Kubernetes Secrets, so why would I use the Vault Secrets Operator (VSO)?”
It’s a fair question, and honestly, if that’s where your mind went the first time you heard about VSO, you’re not alone. But here’s the thing: the Vault Secrets Operator isn’t “making Vault insecure.” In fact, in the right situations, it can increase your security posture.
Let’s break down why this misunderstanding happens, and why VSO can still be a secure, effective choice for many workloads.
Why the Confusion Exists
Vault’s biggest selling point for Kubernetes users is that it helps you avoid storing static, long-lived credentials in Secret objects. By having applications connect directly to Vault, you can:
- Fetch secrets on demand
- Rotate them frequently
- Limit their lifetime to minutes or hours
This reduces the blast radius if something leaks.
So when people hear “Vault will now sync secrets into Kubernetes Secrets”, it’s natural to think that we’ve taken a step backwards. But that’s not the whole picture.
How VSO Actually Works
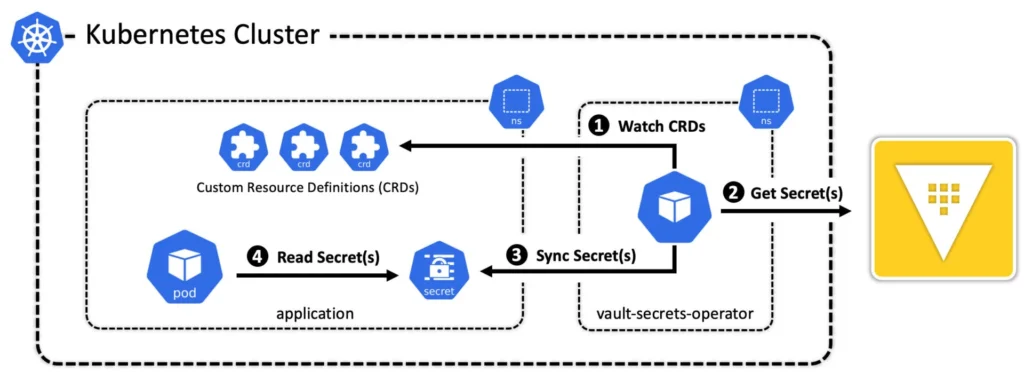
The Vault Secrets Operator still relies on Vault for:
- Dynamic secrets – Generated on demand, with short TTLs that make them useless after they expire.
- Automated rotation – Secrets can be rotated before they expire, keeping workloads continuously up to date.
- Centralized policies – Vault policies still control exactly what secrets an app can access.
Here’s the key difference: VSO syncs these secrets into Kubernetes Secrets objects, making them available to workloads that must consume secrets natively in Kubernetes. That’s the design intent: not to replace direct Vault access, but to support workloads that can’t be modified to pull from Vault directly.
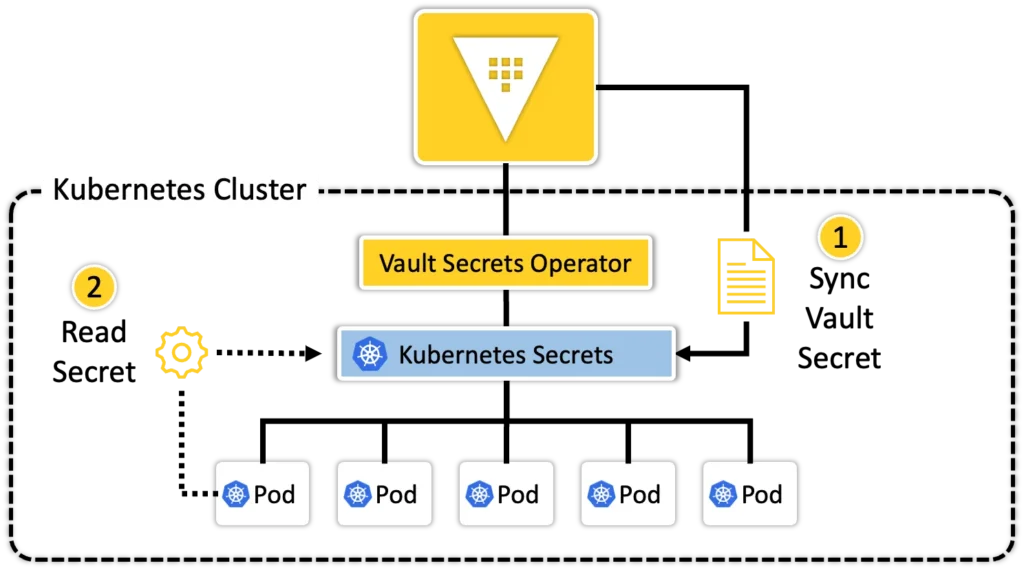
Why VSO Can Still Be Secure
Let’s walk through some security benefits that often get overlooked:
1. Short TTLs = Less Risk
Even though the secrets end up in Kubernetes Secrets, they don’t have to be long-lived. If a secret is only valid for 15 minutes, the window for misuse is tiny, especially compared to a static secret that lives for months.
2. Dynamic Secrets = Frequent Rotation
With Vault dynamic secrets, every pod or client can get unique credentials that are automatically revoked when the pod dies or the TTL expires. This means one compromised pod doesn’t compromise credentials for every workload.
3. Namespace Boundaries Add Containment
VSO writes secrets into the app’s namespace only. Combined with Kubernetes RBAC, this ensures that other workloads in the cluster can’t simply “browse” for secrets they shouldn’t see.
The Role of Kubernetes RBAC
One important point: you still need to lock down Kubernetes access.
If someone can list or get Secrets in a namespace, they can retrieve the synced credentials. VSO doesn’t change that –> you must enforce strong RBAC policies and audit Kubernetes API access.
This is no different than securing ConfigMaps, deployments, or any other cluster object. The operator will do its job, but cluster security is still on you.
Native Kubernetes Authentication with VSO
Another way to strengthen your VSO security posture is by leveraging Vault’s native Kubernetes authentication method. This allows workloads to authenticate to Vault using a Kubernetes Service Account Token, which Vault validates directly against the Kubernetes TokenReview API.
Here’s how it works in practice:
- The workload uses its service account token to request authentication from Vault.
- Vault sends that token to the Kubernetes API server via the TokenReview API to confirm:
- The token is valid.
- The token is bound to a specific service account and namespace.
- If the review passes, Vault issues a Vault token with permissions defined in the role you configured.
Why is this powerful?
- It’s platform-based authentication = no need to hardcode credentials.
- It automatically ties Vault access to Kubernetes identity, which means if a pod or service account is deleted, it can no longer authenticate.
- It provides an additional layer of verification because Vault isn’t just trusting Kubernetes blindly, it’s validating with the cluster’s own API.
When paired with short TTLs and dynamic secrets, this gives you a very strong, identity-aware security model that still works seamlessly with workloads using VSO.
When to Use VSO vs Direct Vault Access
Ideal scenario?
Workloads that can connect directly to Vault and fetch secrets at runtime, especially if they can authenticate securely using something like Kubernetes auth or cloud IAM. This avoids storing secrets in Kubernetes altogether.
Where VSO shines?
When workloads must consume secrets through Kubernetes Secrets. This could be:
- Third-party applications you can’t modify
- Helm charts that expect a Secret to exist
- Legacy workloads where direct Vault integration isn’t practical
In these cases, VSO gives you:
- Dynamic and short-lived secrets
- Automated rotation
- Namespace isolation
- Full Vault policy enforcement
Why Vault Secrets Operator Is Your Secure Kubernetes Bridge
The Vault Secrets Operator isn’t a “step backwards” in security. It’s a practical, secure bridge between Vault’s capabilities and Kubernetes-native secret consumption.
Yes, if you can connect workloads directly to Vault, that’s the gold standard. But for the workloads that can’t… VSO lets you keep Vault’s security benefits while still delivering secrets in a way your applications can use.
So next time someone says “VSO is insecure,” you’ll know that’s not the full story and you’ll be ready to explain why it can actually increase your security in the right use case.
Pro Tip: If you’re deploying VSO, pair it with:
- Short TTLs
- Dynamic secrets
- Strong Kubernetes RBAC
- Namespace scoping
- Native Kubernetes authentication with the TokenReview API
That way, you’ll keep your secrets safe and keep your cluster security team happy.
Note: Make sure to check out my course here, where I include links and coupons to ensure all my content is accessible to everyone.
Explore my latest courses



