If you’ve been working with HashiCorp Vault and Kubernetes for a while, you might be wondering:
“Wait… didn’t we already solve this with the Vault Agent?”
Yep, totally fair question. For years, the Vault Agent Injector has been the go-to solution for injecting secrets into pods using the sidecar pattern.
But now we’ve got the Vault Secrets Operator (VSO) on the scene—and it’s making a lot of people ask:
- Do I need both?
- Is one better than the other?
- Which one should I actually use?
Let’s break it all down.
Note: This content is from my HashiCorp Certified: Vault Associate (w/ Hands-On Labs). Make sure to check it out for additional content on HashiCorp Vault.
Two Common Ways to Integrate Vault with Kubernetes
These days, the two most popular ways to get Vault secrets into Kubernetes workloads are:
- ✅ Vault Agent Injector
- ✅ Vault Secrets Operator (VSO)
Both get the job done—but how they do it (and how they fit into your workflow) is completely different.
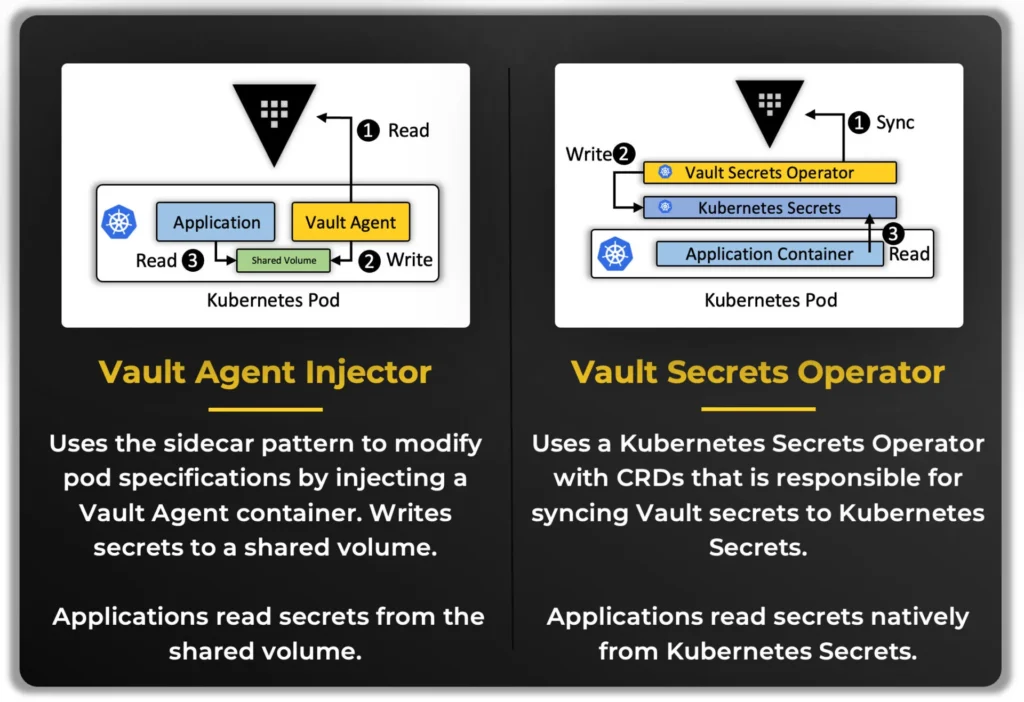
Vault Agent Injector: The Sidecar Approach
With the Vault Agent Injector, we’re working with a sidecar pattern. It modifies your pod spec to inject a Vault Agent container alongside your application.
Here’s how it works:
- Vault Agent handles authentication to Vault
- It pulls the secrets you need
- It writes those secrets to a shared volume in the pod
- Your app reads them as local files—TLS certs, config files, whatever you need
It’s simple and reliable, especially for apps that need file-based secrets or tight control over template rendering and secret renewal.
But it does add a bit of complexity—sidecars, webhooks, extra pieces to manage.
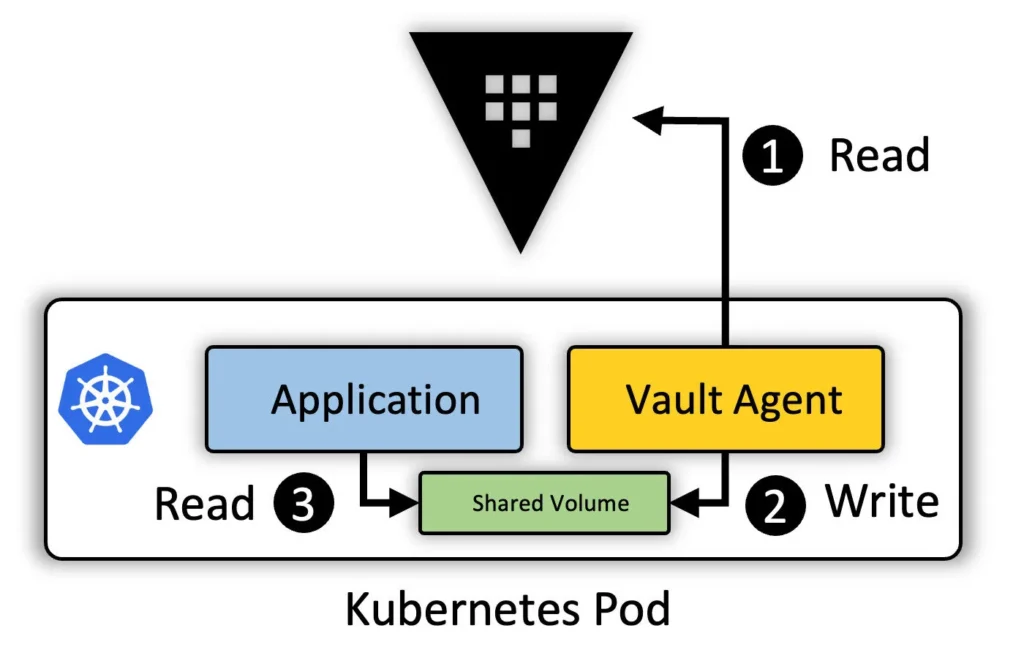
Vault Secrets Operator: Kubernetes-Native Secret Sync
Now let’s look at the newer option—the Vault Secrets Operator.
Instead of injecting a sidecar, VSO installs a controller in your cluster that uses Kubernetes-native CRDs to sync Vault secrets directly into Kubernetes Secrets.
Your app just reads from a native K8s secret like it always has—no Vault logic inside the pod.
This approach fits really well in GitOps workflows, or if you’re managing lots of apps across teams and namespaces.
You define what you want using YAML. VSO handles the sync and the updates automatically behind the scenes.
When Should You Use Each One?
Alright, so which one should you use?
As with most things in engineering… it depends. Here’s a breakdown to help you decide.
When to Use the Vault Agent Injector
Use the Vault Agent Injector when:
- 🔐 Your app expects secrets as files (like TLS certs or config)
- 🔁 You need runtime renewal or re-rendering
- 🛠️ You want fine-grained control using Vault templates
Just keep in mind: there’s a bit more operational overhead here. You’re dealing with mutating webhooks and managing sidecar containers.
When to Use the Vault Secrets Operator
Reach for the Vault Secrets Operator if:
- 🧠 You want a Kubernetes-native, declarative approach
- 🤖 You’re following GitOps, Helm, or other CI/CD practices
- 🚀 You want to make secret delivery simple for app teams who don’t know Vault
With VSO, you describe everything in YAML using CRDs like VaultStaticSecret, and the operator takes care of fetching, syncing, and updating the K8s secrets. No sidecars. No extra containers. Just clean, native Kubernetes workflows.
TL;DR – Choosing the Right Tool
There’s no one-size-fits-all answer. It really depends on your:
- Application’s secret access patterns
- Team’s skillsets and workflows
- Security and operational needs
Choose the Vault Agent Injector if you need low-level control or file-based secrets inside the pod.
Choose the Vault Secrets Operator if you want clean, scalable, Kubernetes-native secret delivery.
Honestly? They both have their place—and some teams even use both depending on the use case.
Just make the choice that helps your team move fast without sacrificing security or sanity.
Note: Make sure to check out my course here, where I include links and coupons to ensure all my content is accessible to everyone.
Explore my latest courses



